
AMD has reversed course and decided to patch the new 'Sinkclose' vulnerability on Ryzen 3000 desktop processors after all. AMD updated its SMM Lock Bypass Security Bulletin, which now includes a fix for Ryzen 3000 desktop CPUs (codenamed Matisse) scheduled for tomorrow, August 20.
Sinkclose is a significant security vulnerability that has affected virtually all AMD processors since 2006. The vulnerability takes advantage of a flaw within the System Management Mode (SMM) in affected chips, allowing hackers to execute code within the SMM. This makes attacks made from the SMM virtually impossible to detect via antivirus software. The vulnerability is difficult to detect and delete and can even persist after an OS reinstall.
Thankfully, this vulnerability is difficult to exploit and requires hackers to use a different exploit to gain access to the computer's kernel before Sinkclose can be used to access the SMM. Regardless, this is a serious vulnerability, no matter how you look at it, and one that AMD is working to patch as soon as possible.
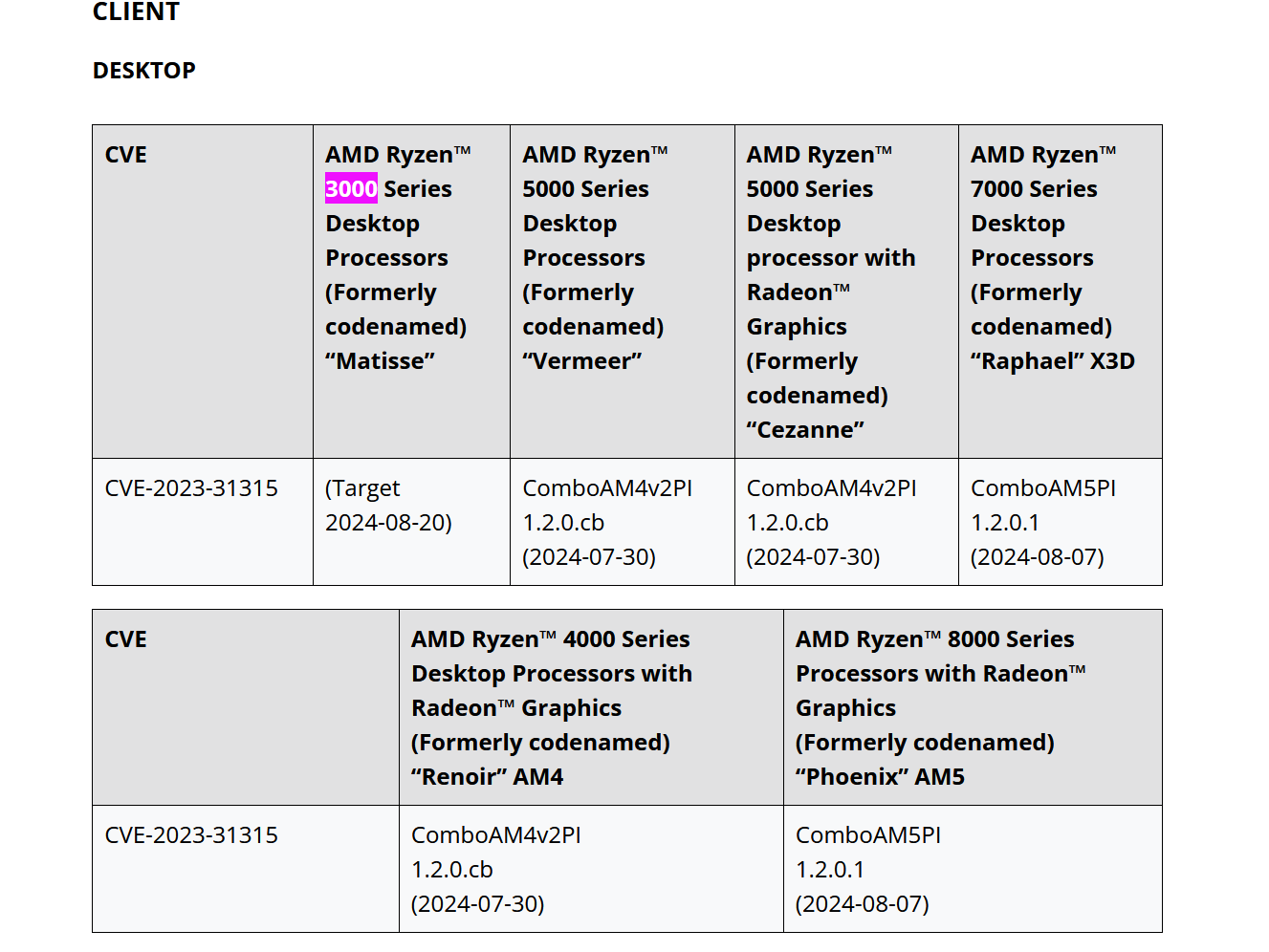
AMD had previously confirmed that it would patch the Sinkclose vulnerability on some of its impacted chips, which include various Zen parts, including server, mobile, and desktop. However, AMD listed Ryzen 3000 as not being planned for a patch, and all of its predecessors were not listed in the advisory at all.
Ryzen Threadripper 3000, Threadripper Pro 3000WX, Zen 2 EPYC (7002), Ryzen 3000 mobile, and Ryzen 3000/4000 APUs all were in AMD's original plans to be patched (and still are).
Thankfully, AMD has officially confirmed a Sinkclose patch for the Ryzen 3000 chips, but it still hasn't listed previous Zen processors. The update for Ryzen 3000 will come out tomorrow. Strangely, AMD did not disclose what microcode update will feature this fix for Matisse processors, even though AMD lists a microcode version for every other CPU lineup getting the fix.
EDIT 8/20/2024: Clarified the processors that aren't listed for a patch.







