
Zen 5 is AMD's first architecture utterly immune to the Inception vulnerability since Zen 3 requires no microcode or software-based security mitigations. Phoronix tested the Zen 5-based Ryzen 9 9950X with all security mitigations on and off in Linux (for other vulnerabilities) to see if there is any performance variance.
Phoronix discovered that Zen 5 features built-in/native mitigation of the Inception vulnerability. Inception is a speculative side-channel attack discovered last year, affecting Zen 3 and Zen 4. Inception enables attackers to access information stored on system DRAM, leading to the leakage of potentially privileged data.
With a native mitigation to Inception, Zen 5 is unaffected by software-based security mitigations' potential performance degradation effects. Zen 3 and Zen 4 require software mitigations to patch Inception. Zen 3 can suffer a whopping 54% performance drop with the Inception software mitigations turned on (but only on specific workloads).
Hilariously, though, AMD's older Zen 1/Zen+ and Zen 2 CPU architectures are unaffected by the Inception vulnerability due to the way the branch predictor works in those architectures.
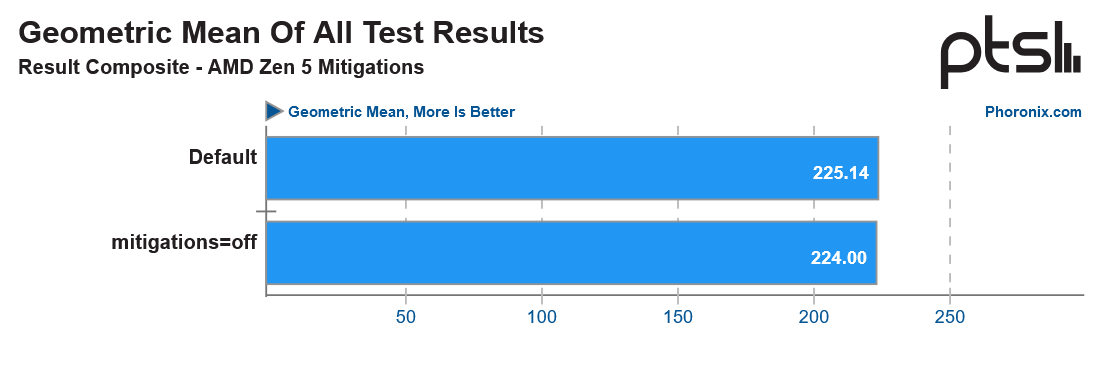
However, despite Zen 5 featuring hardware mitigations for Inception, it still relies on software mitigations for other security vulnerabilities, including Spectre V1. Thankfully, there is virtually no performance penalty with the security mitigations enabled. It is surprising since not all software/microcode-based security mitigations affect performance; it all depends on how the vulnerability affects the CPU and how the mitigation manipulates the CPU.
It would have been interesting to see the Ryzen 9 7950X tested against the 9950X as well to see how Zen 4 performs with and without all of its security vulnerabilities enabled. However, most Zen 5 reviews will already paint this picture since all critical security mitigations are enabled by default on Zen 4 and Zen 5 processors.







