In the occupied far east of Ukraine, Russian forces are aiming waves of missiles against Ukrainian civilian targets. Each of Russia’s state-of-the-art missile launch systems costs more than US$100 million (A$150 million). They allow Russia to launch attacks from safe positions many kilometres behind the front lines.
The S-300 surface-to-air missile launcher is designed to avoid detection. Their locations are closely guarded secrets. However, using publicly available satellite images, we have detected telltale signs of the operation of these weapons that give away their location.
This is just one example of why the strategic and tactical use of publicly available data on the internet has become an increasing source of concern for militaries. So-called “open-source intelligence” (or OSINT) has become a top priority of intelligence agencies worldwide.
As more and more data is digitised and placed online, open-source intelligence has become a powerful tool. Social media platforms, satellite images and leaked data can all be sources of intelligence information.
We have seen significant use of open-source intelligence via social media in the Ukraine conflict. The movements of soldiers and military vehicles have been widely documented. Russian information operations attempting to falsely portray Ukrainian forces as targeting civilians have also been exposed.
Open-source intelligence is a cheap and efficient way for analysts to inform decision-making. In a conflict such as the Russia–Ukraine war, open-source intelligence can act as a force multiplier.
Tracking missile systems online
In 2018, researchers discovered an unexpected use of the Sentinel-1 satellite, a public-access scientific satellite operated by the European Space Agency. It could reveal the location of the United States’ Patriot surface-to-air missile systems. The Sentinel-1 picks up radar emissions from the missile system’s radar, which shows up as bands of interference in the imagery.
Surface-to-air missile systems are usually designed to be highly mobile, so they can be deployed anywhere to surprise enemies. Open-source intelligence means anyone with an internet connection may now be able to locate these assets.
This poses new challenges for military leaders. The strategies and processes they have developed to protect civilians, soldiers and critical infrastructure – as well as their own weapons and other assets – from enemy drones, missiles, or targeted ground assaults may no longer be effective.
How vulnerable are Russian systems?
For Russia and Ukraine, these challenges are playing out in real time. We used Sentinel-1 to locate active and mobile Russian S-300 surface-to-air missile systems in Eastern Ukraine – and if we can find them, so can anyone else.
How did we do it? First, we analysed multiple social media sources for confirmed locations of S-300s. We then viewed Sentinel-1 imagery of these locations and increased the sensitivity to reveal radar interference from the missile systems. The interference patterns show the radar source sits along a certain line.
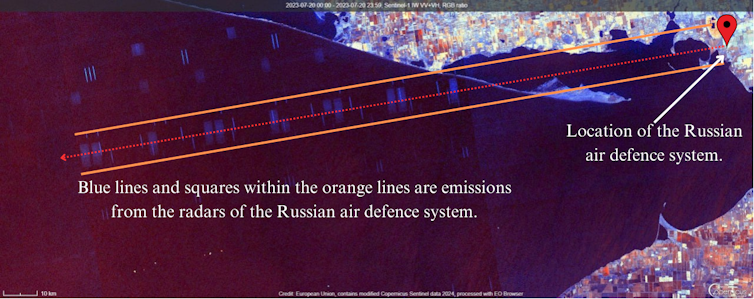
The above image shows how it works. With a known location, it took only a few minutes to acquire the image and reveal the radar interference. This image shows an S-300 system from the Kherson Oblast, a Russian-occupied region of Ukraine, which was neutralised days after the satellite captured the interference.
The S-300 is widely regarded as Russia’s counterpart to the US Patriot system. In Russia’s war on Ukraine, it is tasked with defending against missiles and aircraft but has recently been used to target Ukrainian civilians.
To date, only around nine Russian S-300 missile launchers have been confirmed destroyed over the course of the war. This illustrates how rare and highly protected they are, reserved for protecting the most vital assets and regions of the Russian military.
For better and worse
The S-300 is exported to Iran, China and many other nations. Russia’s is not the only military that may be compromised by the location of S-300 systems through public satellite imagery. Of course, these systems need to be in operation to emit interference.
This grants advantages to non-state combatants and states with less sophisticated militaries. These forces may be able to locate and potentially destroy hundred-million-dollar assets with publicly available data.
Ukraine’s military has shown how efficient low-cost drones can be in destroying expensive air defence systems. Open-source data, such as the electronic emissions collected from scientific satellites, illustrates how ordinary and even innocuous tools can be used for warfare.
The overall ethical implications of open-source intelligence are mixed. Public data may be used by malicious non-state actors or terrorist groups, for example.
On the other hand, analysts and journalists can use such processes and methods of data gathering and analysis to investigate war crimes and abuses of human rights or create more accurate reporting of events. The Institute for the Study of War, for instance, has employed satellite imagery and social media documentation to demonstrate Russia’s military buildup on Ukraine’s borders in 2021 and 2022, thereby exposing Russian intentions.
The future of open-source intelligence
Open-source intelligence, and the critical skills required to examine public data, have become increasingly important for militaries and intelligence organisations. However, open-source data platforms, such as satellite imagery provided by the European Space Agency, are likely to produce ongoing challenges for militaries.
How will the world respond? Institutions, business, government sites and other bodies may decide to cut off the flow of public data in order to reduce its unintentional impact.
This too would create challenges. Censorship of publicly available data would pose risks to transparency of information and degrade public trust in companies and public institutions. Removing public access to information would mean people and organisations with less money could no longer access it.
The authors do not work for, consult, own shares in or receive funding from any company or organisation that would benefit from this article, and have disclosed no relevant affiliations beyond their academic appointment.
This article was originally published on The Conversation. Read the original article.







