Twingate revolutionizes corporate security with its software-defined perimeter platform, enabling IT, security, and DevOps teams to provide secure, remote access to critical business resources. Eliminating the need for legacy VPN solutions, Twingate's powerful and intuitive SaaS solution creates an enterprise-grade security network that's simple to set up and manage, no matter how complex the IT infrastructure is.
Want to try Twingate? Visit the website.
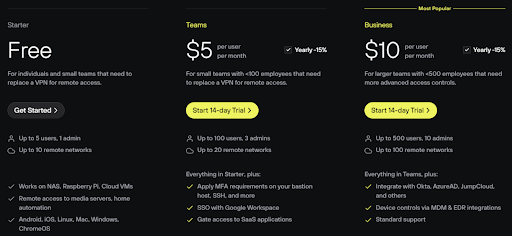
Plans and pricing
Pricing for Twingate starts off with the Starter-free plan, which allows access to up to 5 users and up to 10 remote networks. It’s a great way to test the waters before you decide and purchase the other plans. Following the Starter plan is the Teams plan which costs $5 per user, per month. You can have up to 100 users and 20 remote networks, and there is a 14-day trial or money-back guarantee.
Moving on up, we reach the Business plan at $10 per user per month, meant for large firms with up to 500 employees and up to 100 remote networks. The Business plan offers a lot more integration options compared to the initial two plans, but costs significantly more.
Finally, there is the Enterprise plan, for which you will have to go through sales to agree on a price and customize the features your organization needs.
Features
An advantage of Twingate is that IT teams can easily set up access restrictions - unlike with a traditional VPN (IKEv2 or OpenVPN, for instance) that requires tedious manual adjustments, additional proxies, and brings extra risk. With Twingate, it's all streamlined for effortless permission management.
Twingate offers a proxy connection to allow you access to your business resources - from files to servers and gateways. The process is comprised of four components - the app, controller, connector, and relay - which all work together to ensure secure access to the requested business resource. If the resource is a website that's available normally, you can access it without going through the relay.
Authentication with Twingate is taken to the next level - zero-trust network and application-level filters are used to verify users and provide them with access to only the resources they need. In the case of a security breach, only that particular resource is compromised, instead of the entire network. The system admin has full control over who has access to what with granular permissions for individuals and groups, all managed through one app.
Additionally, Single-Sign-On methods like Okta and Google are used for authentication, with added second-factor authentication through Twingate's native 2FA functionality for added security. No need for a traditional VPN.
Not only does Twingate offer integrations with SIEM solutions and log managers, but it also seamlessly integrates with a wide range of identity providers such as Okta and OneLogin, offering MFA and single sign-on across all user accounts. Furthermore, Twingate integrates with mobile device management and endpoint detection and response vendors, making it easier to manage and provide a clearer view of security across various layers.
Interface and in use
With its user-friendly interface, Twingate makes it easier than ever to use commercial VPN software. Unlike many corporate VPN solutions, the Twingate client runs quietly in the background, requiring no user interaction after you're logged in. End-users don't need to worry about remembering alternate hostnames or IP addresses, either, Twingate will route requests to the right resource, no matter which network you're connected to. All in all, the convenience of Twingate ensures a seamless experience when accessing company resources.
Support
Twingate offers support, though you may not find it available when you need it. It utilizes a ticketing system, messaging, and email for its main forms of assistance. Plus, it has comprehensive guides and FAQs to help with more common issues - and I found these to be really helpful.
Security
Twingate collects some of your information, mostly to set up your account and for diagnostics. While you can voluntarily provide more info, the uses of your data is clearly stated in the privacy policy. Furthermore, since Twingate is integrated with various third-party apps, it may receive additional information.
Nevertheless, don't worry; Twingate can't read any data not routed through it, meaning it won't log your usual personal traffic such as video calls and messages. However, as Twingate is based in the US and part of the 5 Eyes Alliance, it's possible that any member countries could demand your data. If this is a concern, be sure to check out standard VPNs with good privacy policies.
The competition
Okta is one of the main competitors that offers a viable alternative through numerous additional options that Twingate does not offer. The downside with Okta is that if you lack technical know how, choosing the right plan and setting everything up can be a right nightmare. Compared to Okta, Twingate is easy to set up and even easier to use.
Perimiter 81 is another high-priced competitor that seems to do almost everything well. It has great security features and a lot of customization options, but be prepared to pay a premium for its features.
Final verdict
For secure and easy remote access to corporate resources, Twingate is an ideal zero trust network access solution. It offers comprehensive, granular access policy configurations, user activity logging, and an intuitive interface, making it the perfect choice for SMBs or mid-sized enterprises operating in highly regulated industries. With little specialized technical knowledge required and no need to sacrifice the user login experience, Twingate is the go-to choice for secure remote access.







