
Users of recent Canon i-Sensys printers should be wary due to seven critical vulnerabilities, which can be accessed by unauthenticated attackers (h/t DruckerChannel.de). All firmware for the affected printers, up to and including version 3.07, is considered vulnerable. However, Canon has already started to roll out updates, so if you have one of the affected models, update the firmware ASAP.
The specific printers impacted by this issue include the Canon i-Sensys MF750 and LBP670 Color Laser Series, as well as a few i-Sensys X Series printers (X C1333i, C1333iF, X C1333P). These are common and relatively new models, Canon printer users should be sure to double-check their specific model information so they aren't sweating about these vulnerabilities for no reason.
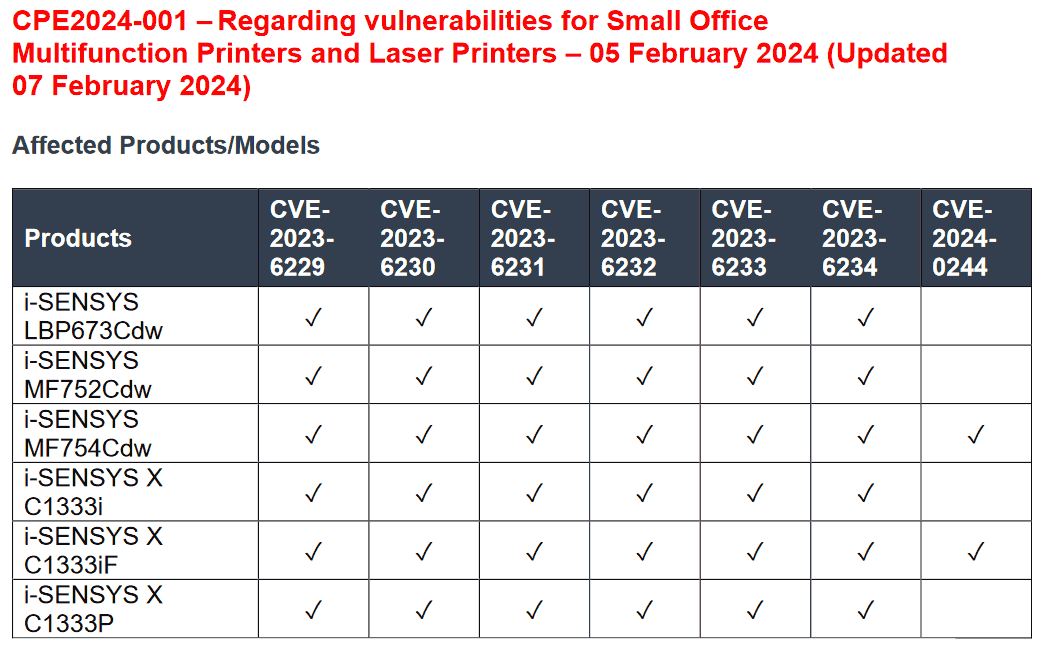
The seven critical security vulnerabilities include such issues as allowing the remote execution of arbitrary code, forcing device crashes, and instigating Denial of Service attacks. Most of these vulnerabilities are also marked as 'critical' according to the Common Vulnerability Scoring System (CVSS), rated as Level 9.8/10 on the severity scale.
Quite a few entities played a part in uncovering these vulnerabilities for Canon. The Japanese firm credits Nguyen Quoc, Team Viettel, ANHTUD, Connor Ford, and an anonymous researcher for identifying these vulnerabilities while working with Trend Micro's Zero Day Initiative. It's nice that Canon is paying attention to the community on this issue, crediting the appropriate parties, and working on releasing fixes as quickly as possible.
Unfortunately, the only real recourse users of these specific Canon printers have is to keep their printers offline, off publicly accessible networks, until the appropriate updates are applied. Unfortunately, we are again facing a scenario where the "smart" version of a device simply introduces more trouble compared to regular old offline hardware.
Thankfully, we have seen that official fixes are arriving from Canon already. For example, users of the affected MF754Cdw and MF752Cdw can grab a new firmware updater here, which specifically states the CVEs in the table above will all be patched.







