
What you need to know
- A security vulnerability dubbed "aCropalypse" could pose a severe data risk to Pixels, custom ROMs, and other Android devices using the default "markup" editing tool.
- PNG screenshots on a Pixel could be unraveled by attackers to rediscover what sensitive information you didn't want others to see.
- The vulnerability has fortunately been patched through Google's recent March feature drop.
A simple and easy-to-do thing like editing a screenshot from your Pixel has become a cause for concern. What's being dubbed the "aCropalypse," researchers Simon Aarons and David Buchanan discovered an exploit with PNG screenshots after some cropping on Pixels using markup (via Android Police). The issue was spotted affecting Pixels, non-Pixel Android phones, and a few custom ROMs, as well as being quite prevalent but not constricted to the messaging service Discord.
Both researchers spotted the severe security flaw on January 2 and they quickly whipped a way to prove its existence before alerting Google later on the same day. After acknowledging it, Google patched the issue internally on January 24 but didn't roll out the fix until nearly two months later with the March feature drop.
The technical exploit apparently goes back a few years due to an API change from Android 10 spotted by the researchers on the IssueTracker. It's said that the markup tool was changed to no longer truncate (shorten) an image file.
In simpler terms, if your original file size was 10MB and after cropping it turned into 3MB, the markup tool wouldn't just throw away your useless photo pieces which would, in some cases, hold quite sensitive information. As researcher Simon explained, "so basically the Pixel 7 Pro, when you crop and save a screenshot, overwrites the image with the new version, but leaves the rest of the original file in its place."
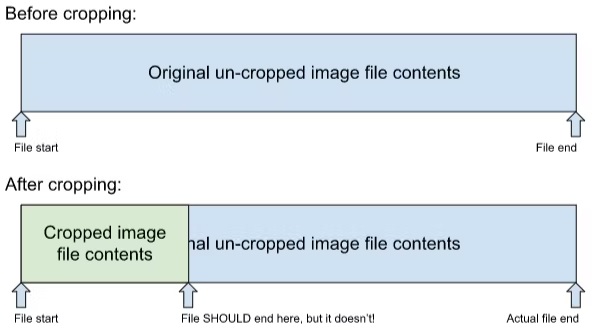
Buchanan posted some information on what a PNG file is and how it operates its data blocks on their blog. A PNG compresses its data into blocks and if a file is edited or cropped, in this instance, one of those existing blocks could contain information from something deleted (or covered up) through the editing process. Buchanan explains, "theoretically, an image could be made up almost entirely of back-references to missing data, but in practice, most images aren’t like this."
Discord is being highlighted because of the way it previously handled user-uploaded imagery. Before January 17, Discord's own processing method never stripped metadata or compressed images. Due to this, the exploit could be taken advantage of on the messaging service.
Both researchers have created a tool that demonstrates this exploits process on screenshots you provide taken from several Google devices like the Pixel 7 Pro. It can be quite daunting to see in action considering any edits made to block out certain information or completely cropped images are back to their full, original forms. Others have chimed in on Twitter with their own screenshots popped into the tester to see that their previously thought discarded scraps aren't truly gone.
It does appear that this problem did not affect JPEG images which could be due to the differences in how each file type handles data. However, even with the March update, older edited PNG files that have already been sent could be exposed.
Introducing acropalypse: a serious privacy vulnerability in the Google Pixel's inbuilt screenshot editing tool, Markup, enabling partial recovery of the original, unedited image data of a cropped and/or redacted screenshot. Huge thanks to @David3141593 for his help throughout! pic.twitter.com/BXNQomnHbrMarch 17, 2023







