Intel has been in hot water over the past couple of months as the Raptor Lake chip degradation issue transpired. While the latest 0x129 microcode patch update, as per Intel, resolves all related problems on new processors, OEMs mainly released this microcode through BIOS updates. As per a report by Phoronix, Intel is now packaging this microcode in the Linux Kernel, so users can easily install the update without tinkering with the BIOS.
The latest Intel Microcode 20241029 release for Linux includes this crucial patch alongside a few other fixes. However, users with already degraded processors will still have to pursue an RMA since their chip is likely cooked. A large part of this fix was to address the significant rise in the minimum voltage supplied to the CPU (Vmin), enforcing a hard 1.55V limit. This patch is part of an entire trilogy of microcodes and fixes, each aimed at solving a different problem.
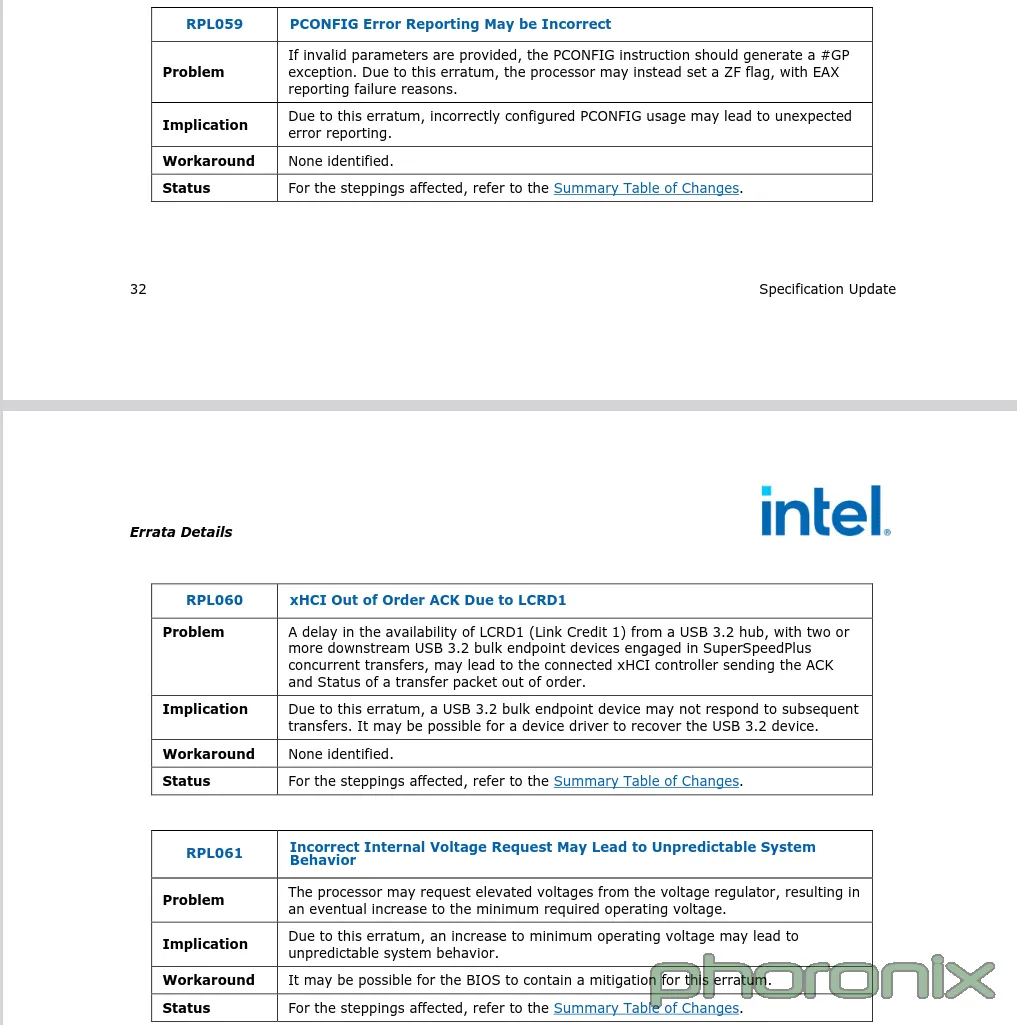
Two smaller issues have also been mentioned in the patch notes of this microcode. This includes the xHCI controller sending out-of-order packets owing to a bug in the USB 3.2 hub and incorrect PCONFIG error logs.
So, what does this entail for the average user? Microcodes are small low-level instructions that reside in specific registers within the CPU. Post-manufacturing, AMD, and Intel frequently update these microcodes to resolve security, stability, and even critical issues such as the one we're discussing right now. Microcodes can be updated by the BIOS or by the Operating System. The former is offered in the form of BIOS updates by OEMs but is a bit harder to follow for the average consumer. Unlike your Operating System, the BIOS generally doesn't notify you when new updates are available. The onus is on the user to keep an eye on the support page for their motherboard.
Enter plan B - updating through the Operating System. It is very rare for microcodes to be available on the OS level and if so; do not skip them! This method ensures that the patch is accessible to the majority of people. Once the update has been pushed out to everyone, impacted users can open their package management utility in Linux and update with the click of a button or a simple terminal command.
Most distributors will integrate this patch into the package manager. If you wish for a custom installation such as an early load update or a late load update, you can find more details over at the GitHub repository.







