YouTuber Eric Parker demonstrated in a recent video how dangerous it is to connect classic Windows operating systems, such as Windows XP, to the internet in 2024 without any form of security (including firewalls or routers). The YouTuber set up a Windows XP virtual machine with an utterly unsecured internet connection to see how many viruses it would attract. Within minutes, the OS was already under attack from several viruses.
It might seem silly to hook a PC up to the internet purposefully without using any security. However, in the early 2000s, catching a PC directly to the internet without a router was normal. Granted, Windows XP has a built-in firewall, and most people used anti-virus software at the time. Still, running in a completely unprotected state (intentionally or accidentally) was much easier than newer operating systems. On top of this, running Windows XP unsecured in 2024 is even more dangerous since the operating system no longer receives security updates, making it very easy for hackers to get into the OS.
Two minutes after hooking up his Windows XP virtual machine to the internet, Eric Parker found a couple of viruses that randomly installed themselves on the machine, including a virus dubbed "conhoz.exe." Soon afterward, another virus automatically created a brand new Windows XP account dubbed "admina" that apparently was hosting an FTP file server on the machine.
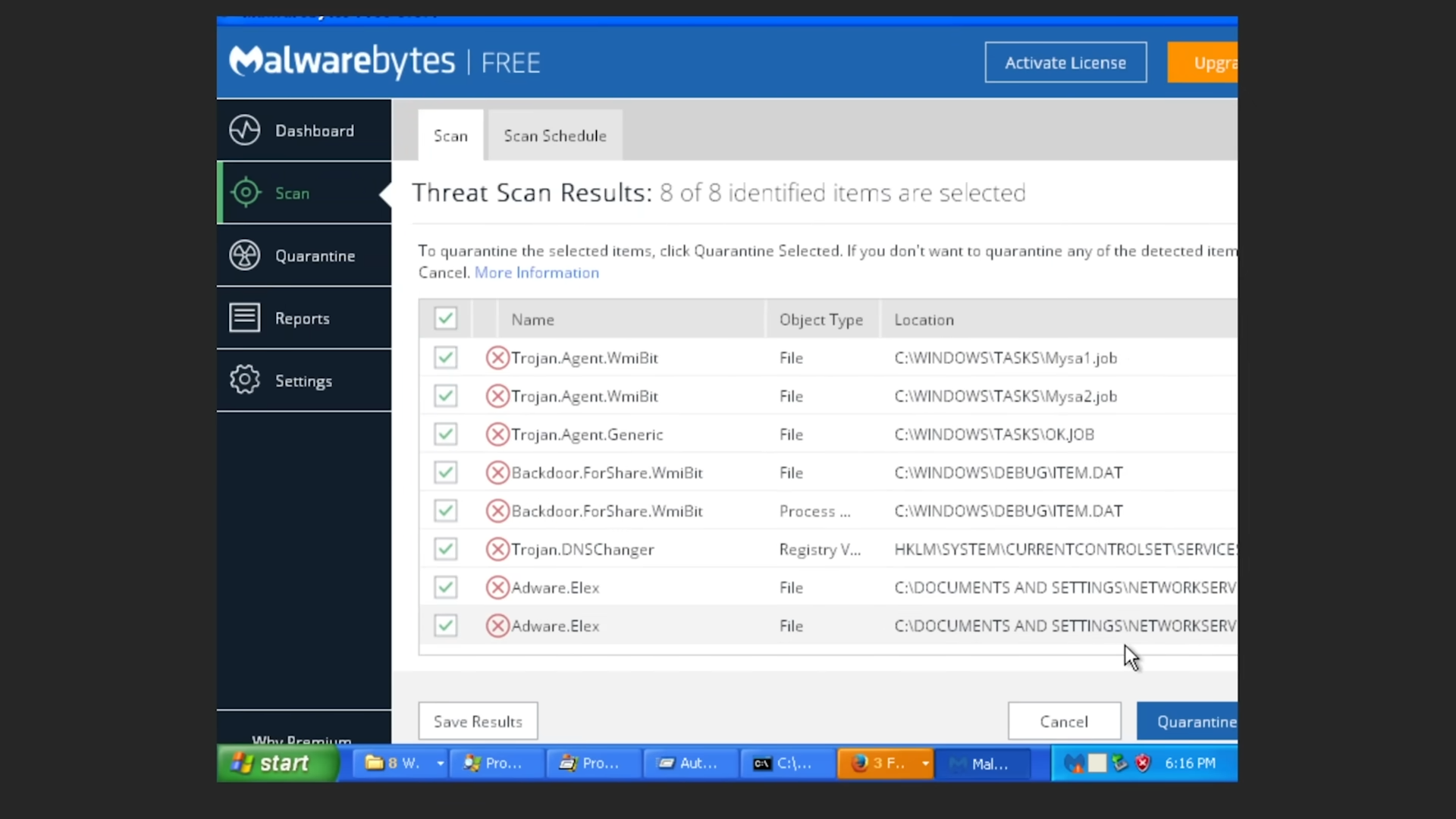
It didn't take long for many other trojans, viruses, and malware to appear on the system. Eventually, Eric Parker installed Malwarebytes on the XP machine to see how many viruses it would catch. It caught eight viruses classified as trojans, backdoors, DNS changers, and adware. There were still more viruses on the machine, but the free version of Malwarebytes Eric Parker used was only able to catch eight of them.
Windows 2000 suffers a similar fate
Eric Parker also did the same experiment in Windows 2000 and discovered even worse effects on the older OS. Within minutes of exposing the OS to the internet (and ensuring all ports are open, including ports for SMB), a virus installed itself on the computer and automatically shut down the virtual machine. After restarting the VM, more viruses appeared, eventually causing the operating system to blue screen.
These two demonstrations represent a worst-case scenario for both operating systems. Without the most basic security measures, online hackers can use tools such as nmap to detect the specific operating system version a vulnerability system is running and able to freely download and run viruses and malware directly on the system once they know it is a system that is vulnerable.
This sort of severe security vulnerability does not exist in modern operating systems. Windows 10 and Windows 11, for example, have far more robust security measures that prevent malware from simply installing itself, even if the firewall is turned off. Eric Parker confirmed that Microsoft operating systems dating back to Windows 7 are unaffected by the previously demonstrated security vulnerabilities. He ran Windows 7 for hours without an anti-virus or firewall on another VM and did not detect any viruses on the system.







