
A word coined accurately: a malvertising campaign has been running ads on Google search, pretending to be a widely used legitimate and non-malicious system information tool CPU-Z. This deceptive campaign has been running ads via Google Search, tricking users into downloading its version of CPU-Z containing the Redline info-stealing malware. While some users may have browser protection and anti-virus apps that would normally detect this, the installer has been digitally signed yet contains a malicious PowerShell script, thus aiding in evading detection.
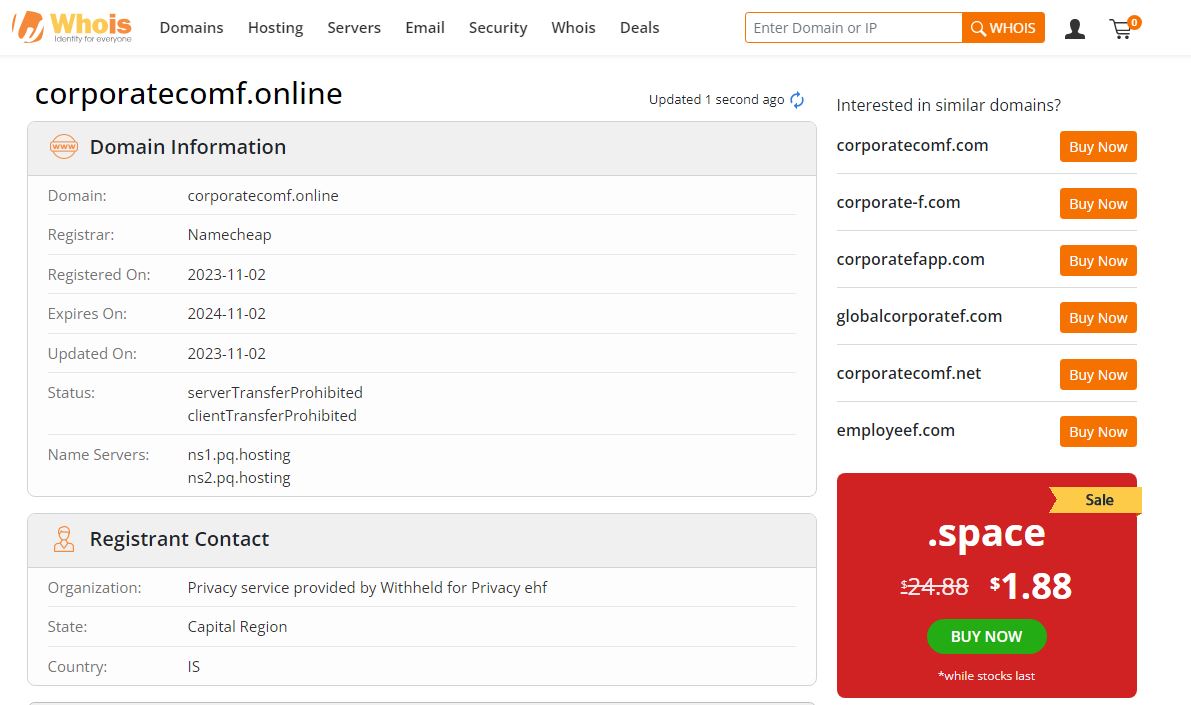
One such website was created, and this campaign ran from November 2 until the time the owner turned off the website. According to WHOIS information at the time, the domain name is from Namecheap, and PQ Hosting hosts the website server. It should be also noted that according to Whois details, this was updated one day ago at the time of writing, so it is likely the website owner may have changed the website hosting server and kept it disabled.
Attacks using CPU-Z's trust and familiarity among users aren't new; it can be traced as early as 2021. Some even claimed to provide CPU-Z installers, only to first download and install itself as a downloader.
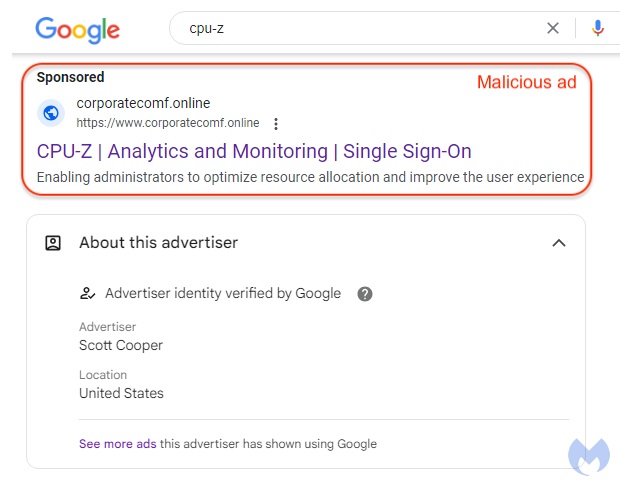
The best of us can fall for it since Google doesn't highlight ads with different font colors or visible borders separating itself from organic search results. While banner ads are obvious, word-based ads with links can be easily exploited. The rest depends on the website design (based on one of the reported domain names, the URL name doesn't seem to be a factor with some users who fall for this). With specific keyword and geolocation targeting, people running such malicious campaigns infect plenty of users before they get reported for website violations.
Similar Campaigns With Notepad++
This malwaretisement campaign is similar to what was seen with Notepad++, which can be traced back to 2021. Some Notepad++ users unknowingly downloaded the app from an ad that's placed above the search results and exploited the system using the same method.
According to the source, RedLine Stealer is a malware that was discovered in March 2020. It was also discovered to be masquerading as a privacy tool as early as July 1st, 2021.
Issue With Google Ad Policies and Web Hosting Servers
Google does have policies against such websites, but even if Google checks the website and downloadable content for any malicious software, it isn't difficult to change the downloadable content after the ad is approved. This is a challenge the ad network and hosting companies need to resolve.
Starting a website for cheap is effortless, and giving fake registration details and information to a web registrar and hosting company takes no effort. With the acceptance of cryptocurrency by certain hosting companies, it is easy to bypass the need to give genuine information via credit card or have the ability to blacklist a user based on credit card credentials.
Seeing that this can be a profitable venture, it's unsurprising that similar campaigns are used against well-known apps like Notepad++ and CPU-Z. Until Google adds further safeguards or at least highlights word-based ads in Google search results clearly, users will need to keep an eye out for 'sponsored ad' wording above the link and notice the website's name indicated in the ad and the search result.
As per usual, it is also best not to dismiss warnings from security apps, assuming it could be a false positive. Having that eye to see the bad giveaway is the only way forward for now.







