
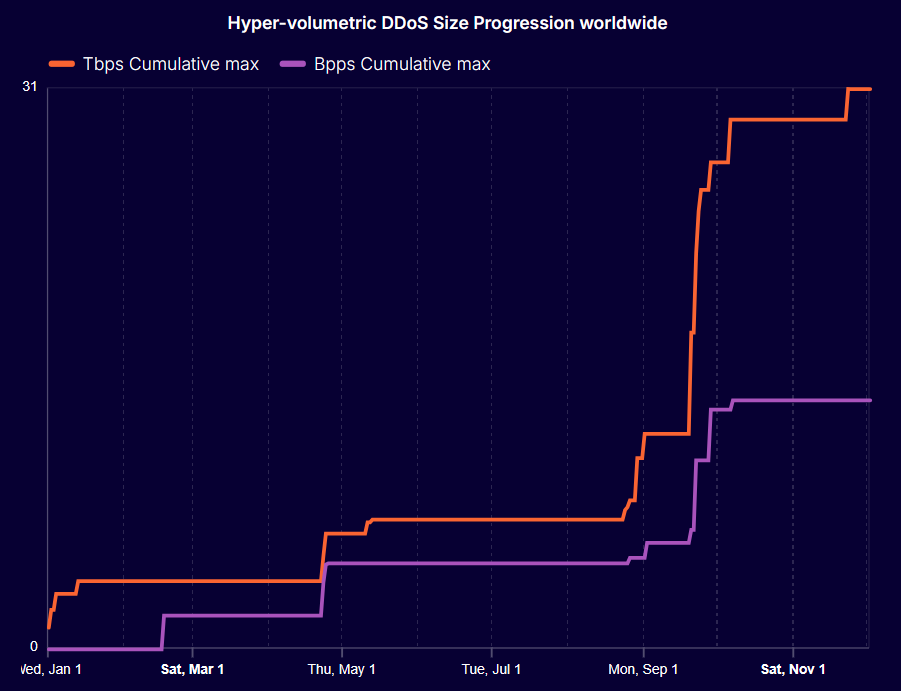
Distributed denial-of-service (DDoS) attacks have become an unfortunate routine part of the modern internet, with botnets of compromised devices spreading ever wider. Unfortunately, the scale and frequency of those attacks have also been rising. The Aisuru-Kimwolf botnet recently smashed its previous record, hitting 31.4 Tb/s in December. To put it into perspective, that's bandwidth enough to stream nearly 2.2 million Netflix 4K movies at once.
An attack of that dimension is enough to easily knock many internet service providers offline, if not entire countries. In a blog post (via BleepingComputer), Cloudflare calls it an "unprecedented bombardment" targeting its customers, dashboard, and infrastructure. The company notes that these attacks are performed in a "hit-and-run" fashion, with gigantic bursts of traffic hitting everywhere at once, lasting from a few seconds to minutes.
Cloudflare also notes that the potential attack size grew by 7x in a single year, thanks to the growth of the Aisuru and Kimwolf botnets. Aisuru is considered the "parent" botnet and comprises small, internet-connected devices such as IoT equipment, DVRs, and even virtual machines on hosting services. Aisuru's devices reportedly live primarily in the U.S. The botnet grows by gaining access to new devices via default credentials (e.g., username "admin", password "admin") and outdated firmware that contains known vulnerabilities.
As for Kimwolf, it can be regarded as a variant of Aisuru, but explicitly targeted at Android-based devices: mobile phones with outdated software or malicious apps, smart TVs, and set-top boxes, among others. Cloudflare says most of Kimwolf's two million minions live in Brazil, India, and Saudi Arabia.
The operators of the botnets have an interesting economy that they operate within. They sell access to the botnet to other cybercriminals, sometimes at surprisingly low prices, for tens of thousands of dollars. The renters then use the botnet to spread their malware, spam, or whatever nefarious activity has been scheduled for the day. The received funds help expand the botnet further.
Cloudflare does note that the Aisuru-Kimwolf network is "parasitic" and that its owners rent out "residential proxies", a term describing a set of devices in a residential setting, adding a layer of anonymity for attackers to hide behind.
On the technical side, UDP carpet-bombing is apparently the most commonly used technique, and the one employed for the 31.4 Tb last December. That entails spreading out the attack surface so wide that it makes it hard for the defenders to block it. Cloudflare adds that the combined botnet has also been targeting gaming services with hyper-volumetric HTTP attacks, sending gigantic amounts of legitimate-looking requests to online services that ultimately overwhelm the target's network or computing capacity.

Follow Tom's Hardware on Google News, or add us as a preferred source, to get our latest news, analysis, & reviews in your feeds.







