What you need to know
- BitLocker is the built-in encryption solution for Windows Professional Edition.
- It has been historically very secure and an excellent encryption option to safeguard your data.
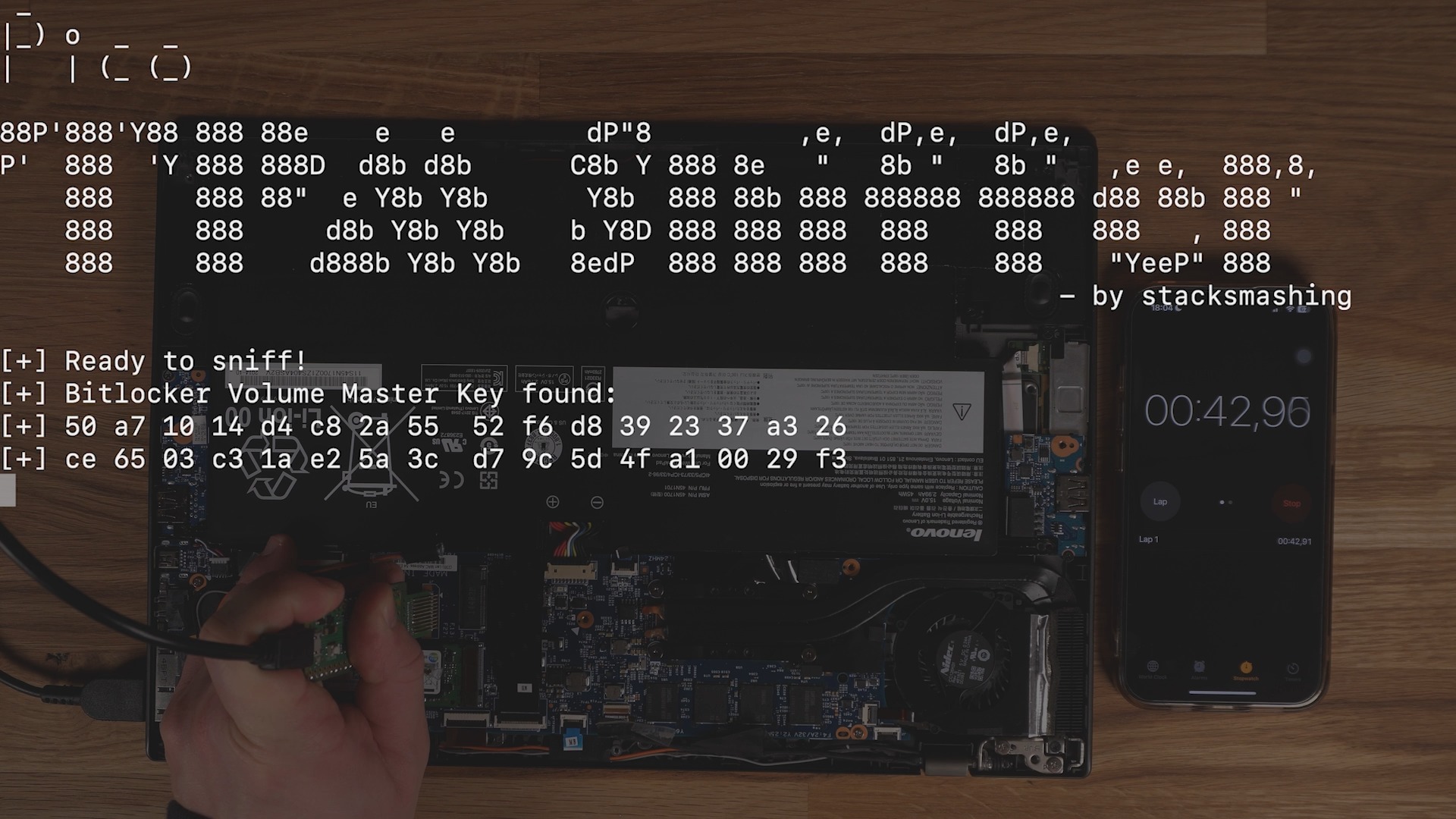
- YouTube creator Stacksmashing released a proof-of-concept video showing how a Raspberry Pi Pico can sniff the Master Key from an external TPM to breach BitLocker encryption.
One of the few things you can do to secure your Windows PC is to enable BitLocker. This has been tried and true advice from cybersecurity experts for years. That being said, a new vulnerability has been discovered by the YouTube channel Stacksmashing. The hack shows a method of sniffing the Master Key in transit from the External TPM to the CPU due to them being unencrypted. While it might be possible to patch this, I don't think it will be viable as it would likely require a hardware solution.
This was possible with a Raspberry Pi Pico, usually under $10. If you have an older PC with an external TPM, look into securing your data using other methods, such as locking your folders or using cryptography to encrypt with EFS.
How was it done?
Stacksmasher discovered that during bootup, a device must send something to the CPU to tell BitLocker to enable bootup, and it might be possible to intercept or sniff that traffic. Using the custom-configured Raspberry Pi Pico, the user placed leads directly on the connectors on the motherboard to access the LPC bus that handled the traffic between the external TPM and the CPU.
The Raspberry Pi then used customer software written by Stacksmashing called TPM Sniffer to read the binary data sent across the LPC bus and attain the Bitlocker Volume Master Key.
"During boot, the different components of the system, for example, the BIOS, hash their firmware and their configuration and send that hash to the TPM. This process is called a measurement. We basically measure the current configuration of the hardware. On the TPM, this hash is used to update so-called PCRs: Platform configuration registers [...] if the PCR is correct, the TPM will unseal the key."
TPM stands for Trusted Platform Module and is important to BitLocker and other encryption methods. A Trusted Platform Module (TPM) is a secure, tamper-resistant chip that generates, stores, and safeguards encryption keys. Typically built into the motherboard, it's also available as a standalone module for system integration.
It is important to note that the TPM is built into the CPU for most current CPUs and PCs, and this vulnerability would not apply. If your PC is using an external TPM, though, your data could be at risk if your device falls into the wrong hands. There are other methods to protect your data beyond just BitLocker if you have an external TPU, as discussed above.
Should I be concerned about this hack?
No, this vulnerability shouldn't apply to your hardware unless you're running an older PC with an external TPM. Also, the only way an attacker could achieve this is if they had extensive hands-on time with your device. If you keep your devices safe and secure, you have less risk of falling prey to this attack method. That being said, new and interesting vulnerabilities are always discovered, and we should always take extra precautions to protect our data and personal information.
If you want to learn more about hacking, discovering vulnerabilities, and defending against cybercrime, check out our guide on how to get started in Cybersecurity.







