
Takahiro Hauryama, a senior threat researcher at VMware Carbon Black, identified and documented thirty-four vulnerabilities in drivers for legacy devices in the Windows Driver Model (WDM) and Window Driver Framework (WDF). Some of these vulnerabilities belong to, but are not limited to, AMD, Intel, Nvidia, Dell, and Phoenix Technologies.
These vulnerabilities reside in either software, BIOS, or the OS drivers for legacy devices, leaving a system open to varying attack vectors that allow nefarious actors full system control so they can conduct any number of attacks, like adding malicious code, altering system privileges, and erasing some I/O instructions, among other possibilities.
Proof-of-Concept
As always, a proof-of-concept is needed to identify and evaluate the seriousness of these vulnerabilities, which the researchers have provided. As with many responsible security experts, Takahiro Hauryama and others who collaborated with him have contacted the responsible vendors.
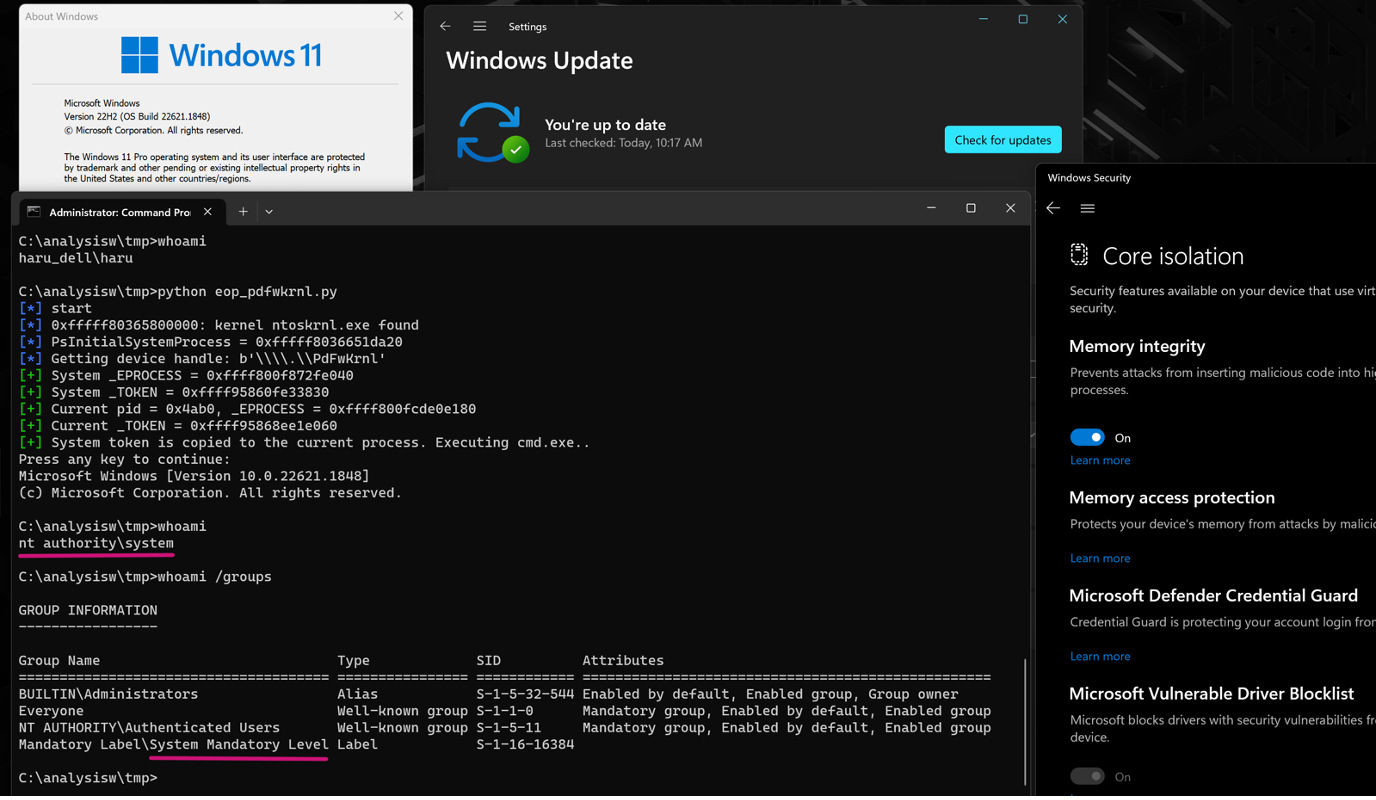
The researcher provided proof-of-concept on an AMD driver filename PDFKRNL.sys. It shows that a non-privileged user could run cmd.exe with a system integrity level by exploiting Windows 11 with Hypervisor-protected Code Integrity (HVCI).
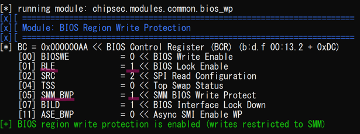
One of the PoC shows firmware erasing exploits specific to Intel Apollo SoC-based platforms. It targets devices by erasing the first 4KB of its firmware in SPI flash memory. This method is similar to an spi erase command, but it also exploits port- and memory-mapped I/O. Another key exploit mentioned in the blog shows the ability to disable BIOS lock and Intel Boot Guard.
It should be emphasized that some of these drivers have expired certificates, and some are even revoked. But the list does include drivers with active certificates.
Other proofs-of-concept can be found in the blog post and Github, which also contains IDAPython scripts.
Vendor's Response
Takahiro also mentioned that JPCERT/CC is coordinating fixes with the respective vendors, and at the time of writing, PC BIOS maker Phoenix Technologies and AMD were reported to have fixed the vulnerabilities with two of the drivers whose signatures were still valid. It was later added that Intel fixed the exploit found in stdcdrv64.sys filename.
Michael Haag, the senior thread researcher at Splunk, also added these findings to his website. This site curates a list of Windows drivers that are found to have a security control bypass that allows the execution of malicious code. Brian Baskin is also credited for supporting this key research.
.jpg?w=600)






